One week out from Patch Tuesday and it’s been a bumpy release for the month, especially for older versions of Windows 10 and Server 2016. (Less affected: the consumer versions of Windows 10 2004 and 20H2.)
Windows Server 2016/1607 suffered the worst of the issues: the original version of the Servicing Stack update KB4601392 caused patching to get “stuck.” Server patchers had to jump through a ton of hoops to get the monthly security update installed. Microsoft pulled the bad update and replaced it with KB5001078. If you were unlucky and installed KB4601392 before it was pulled, Microsoft has this guidance to manually reset Windows updates components.
Windows Server 2016 long has had a reputation of being a horrible platform to patch. It installs updates slower than Windows Server 2019 and typically takes longer to reboot afterwards — and Microsoft won’t (or can’t) backport the fixes from Server 2019 to the older platform. Unlike Windows 10, if you purchased Windows Server 2016 for your firm, you can’t upgrade to Server 2019 for free; it’s an additional purchase. (Given all of the patching issues on that platform, Microsoft, should provide a license to Server 2019 for free for affected businesses.)
If you still run Windows 10 1909, you too were impacted by a buggy update: KB4601315. I personally noticed on my 1909 workstation that I wasn’t offered that update; I only received this month’s .NET patch. I checked around on Askwoody.com and found I wasn’t alone. Others experienced the same issue, especially on consumer versions of Windows 10. Two days after Patch Tuesday, Microsoft released KB5001028, an “out of band” release to fix a blue screen that occurred when you attempted to use a Wi-Fi Protected Access 3 (WPA3) connection. Microsoft notes that you are more likely to encounter this issue when reconnecting to a Wi-Fi network after disconnecting, or when waking from sleep or hibernation. (This is a cumulative update ,so it can be installed on top of, or instead of, the earlier February update.)
Often people question why Microsoft’s pre-release beta testing Insider program, can’t find issues like this. The underlying problem is that the Insider program is testing code for future releases of Windows, it’s not testing patches and updates on the older releases most people still use. We’ve long complained about the lack of quality control with Microsoft updates and, unfortunately, this appears to be another less-than-stellar set of releases.
Microsoft for many years has published a tool that helped us block a troublesome update until we were ready to deal with it, or until the update had a fix released. Called the Wushowhid.diagcab tool, we’ve used this to block buggy updates for years. In the last few weeks, however, Microsoft pulled the tool from its website with no explanation why. Where is this wushowhide tool?
When you go to the web site detailing how you can block a buggy patch or driver, the download link is now a broken link. We think this was triggered by Microsoft wanting to retire any web download that relies on SHA1. But in doing so, many of these older, still useful, tools are no longer available — meaning we have to find them on third-party sites. We no longer have an “official” site for these tools.
I want you to do me a favor. Visit the web site where we used to download the
 Microsoft
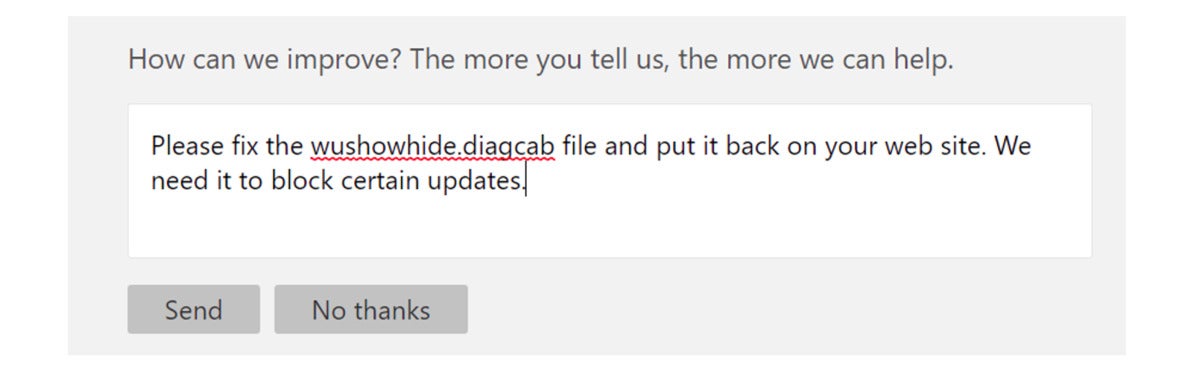
MicrosoftHere’s where you can tell Microsoft to restore access to the Wushowhid.diagcab tool.
tool and scroll to the bottom of that page. Where the footer links to the question, “Was this information helpful?” and asks for a Yes or No, click on the No button. When it asks “How can we improve? The more you tell us, the more we can help,” respond with something like this: “Please fix the wushowhide.diagcab file and put it back on your web site. We need it to block certain updates.” And hit send. I’m hoping that if enough of us provide feedback that we need that tool in particular Microsoft will re-release it.
Getting rid of SHA1 isn’t the issue; it is an older technology and it allows attackers to spoof downloads and content that could be used in attacks. But it’s not cool that we have now lost key tools to keep our systems functional. I’ve recently recommended using the Wushowhide.diagcab tool to block certain updates that would attempt to install over and over again with no resolution. I recommended to someone affected by KB4535680, the update for secure boot that wouldn’t install, to use this tool to hide the update. At the time I gave that advice, the tool was still available. Now they’d have to try to find it on a third-party site. I’d rather be able to point to an official tool on an official Microsoft web page.
For those of you running Windows 10 1909 with Conexant audio drivers, Microsoft is still indicating that the only way to work around an ongoing driver issue is to let the 2004/20H2 feature release install and then when it fails, and rolls back to 1909, let the process install a second time. I remain unsure whether Microsoft will make this process better for these impacted customers. Stay tuned.
So what do I recommend at this time? Be patient. I’m still in testing mode to make sure I don’t see any issues. Thus, I recommend staying in “pause” mode when it comes to this month’s updates. We’ll keep you informed here and over on Askwoody.com of any of the details.



